http://www.youtube.com/watch?feature=player_embedded&v=3u5u5A8_SE0#at=77
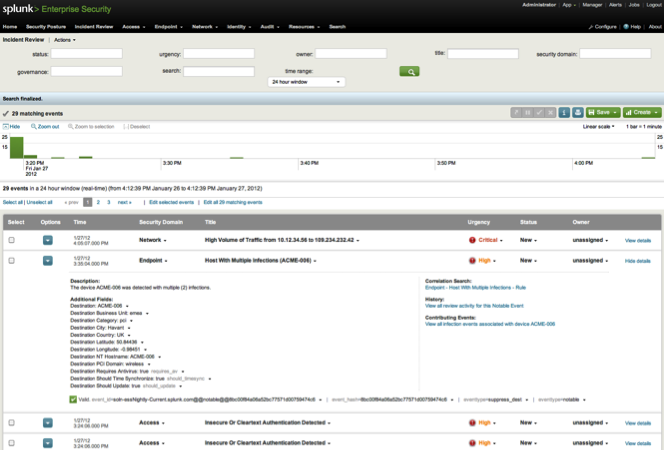
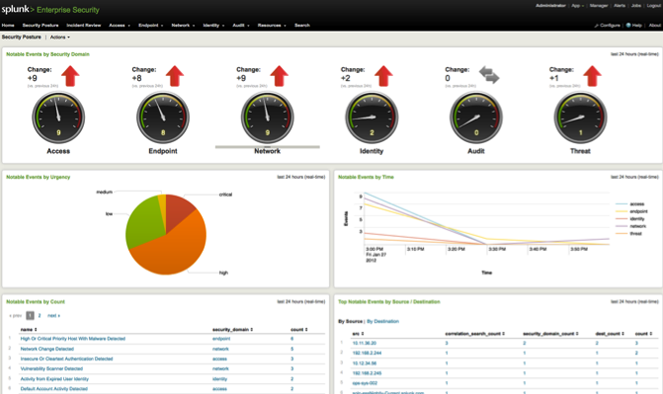
The National Institute of Information and Communications Technology (NICT) a Japanese research institute focussing on different areas in the field of ICT has developed a system for detecting and visualizing attacks on networks. Information about attacks and possible alerts is presented in a rather sophisticated visual way.
There is not a lot of information about the project except a short text and a video showing the system in action. According to the video, the Internet is represented by a wireframed 3D globe in the middle of the screen surrounded by several donut charts each one representing a network. The donut chart shows with two colors (black and blue) which IP-adresses are used (blue) and which ones are not used. Alerts associated with certain IP-sources and -destinations are marked on the donut chart with a sign. These can be clicked to get more details about the alert. The application is supposed to be used in conjunction with a security system, so it’s not a standalone SIEM or something comparable.
There is not more information about how to interact with the system. It seems interaction with the system is rather limited, functioning more as a general visual overview. Though it’s an interesting visualization, I think a question about the practical quality of the system might be justified. It seems like without the ability to filter the visual representation by certain attributes it might be difficult to differentiate important information from negligible. Also, it’s not clear why they use a wireframe globe to show connections to the web. Without the geographical information it seems rather odd because lines going to certain points on the globe don’t provide you with additional useful information. Another question arises when looking at the donut charts: What does the position of IP-adresses on the ring segment express? Is it random? Might have been helpful to show the actual network topology or show the network structure by other visual means in a simpler manner, so we could see which parts of a network are attacked by what countries for example.
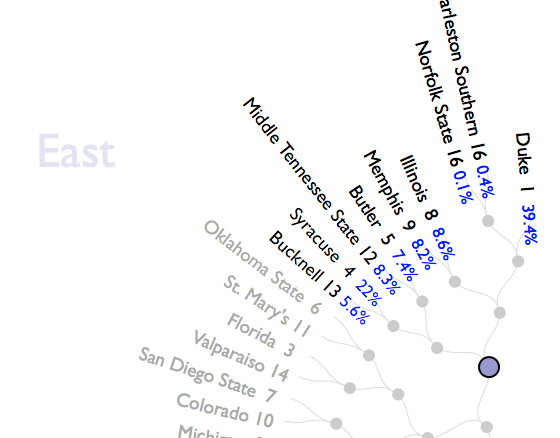

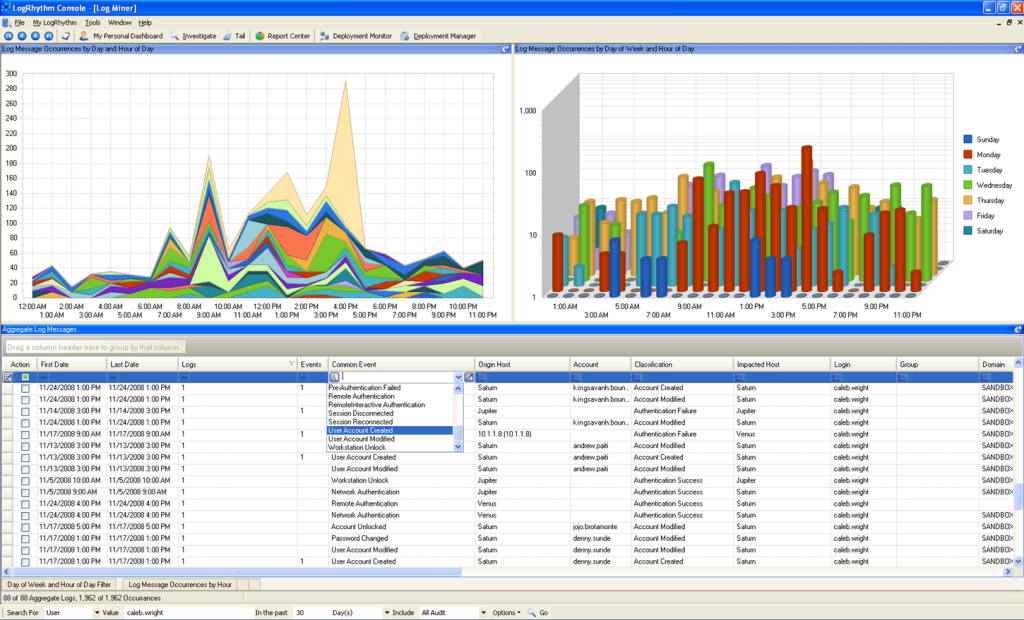
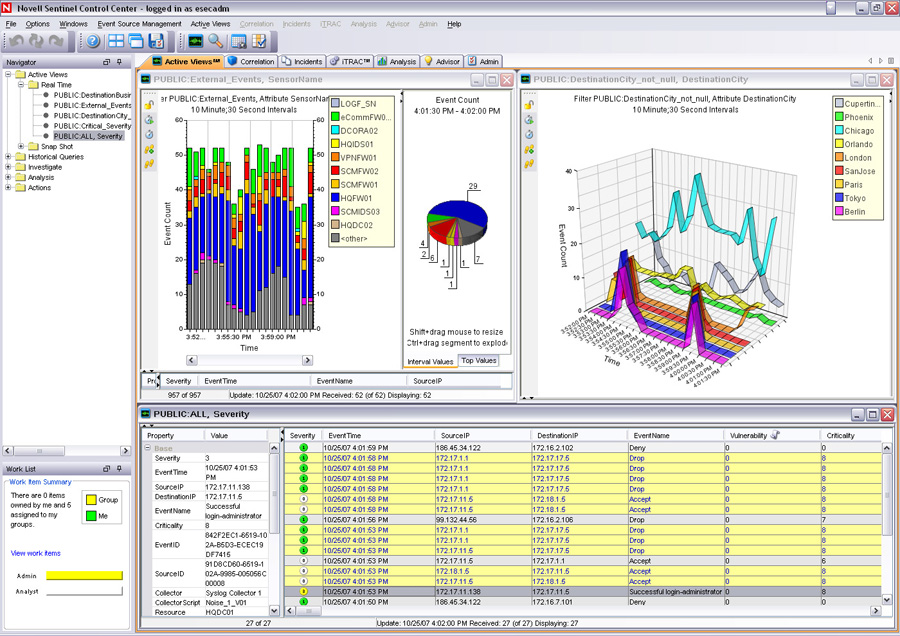
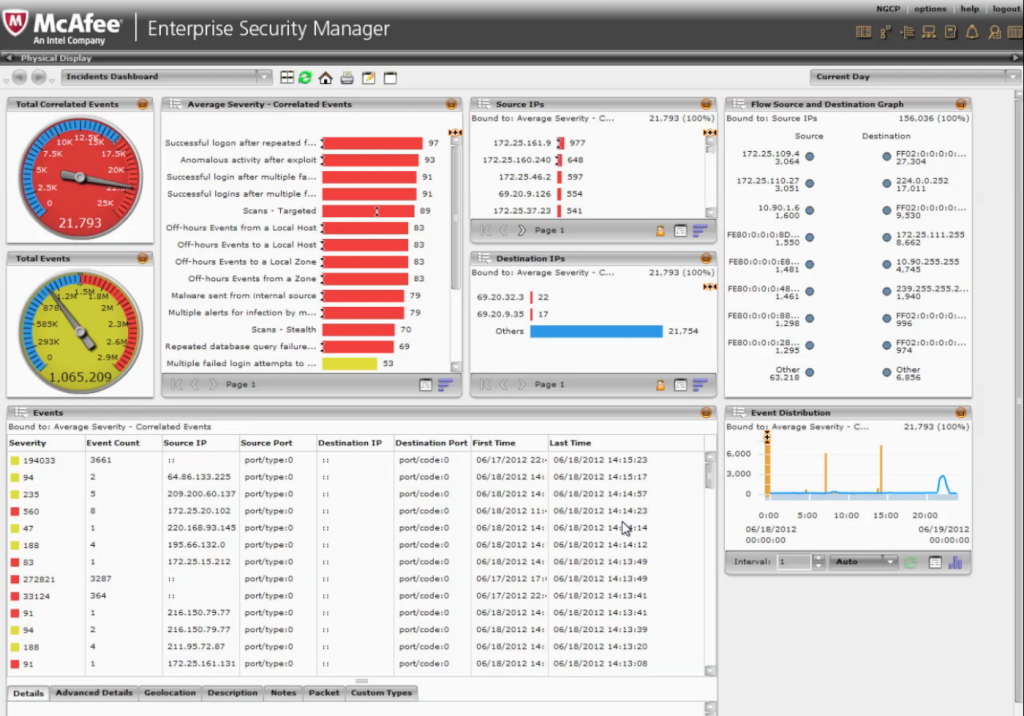
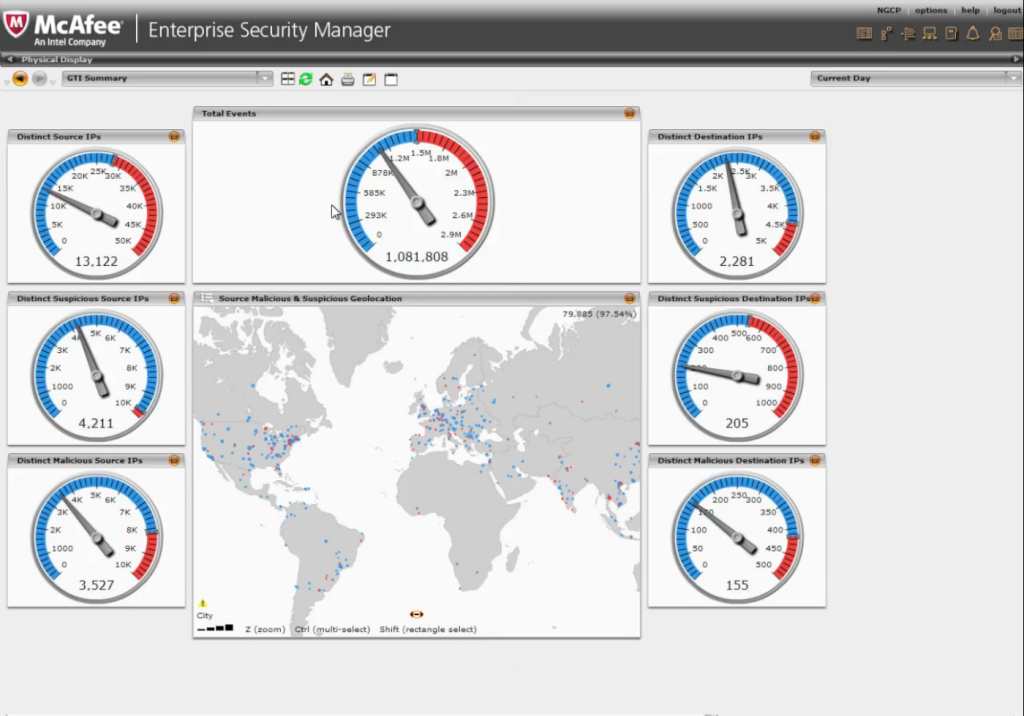
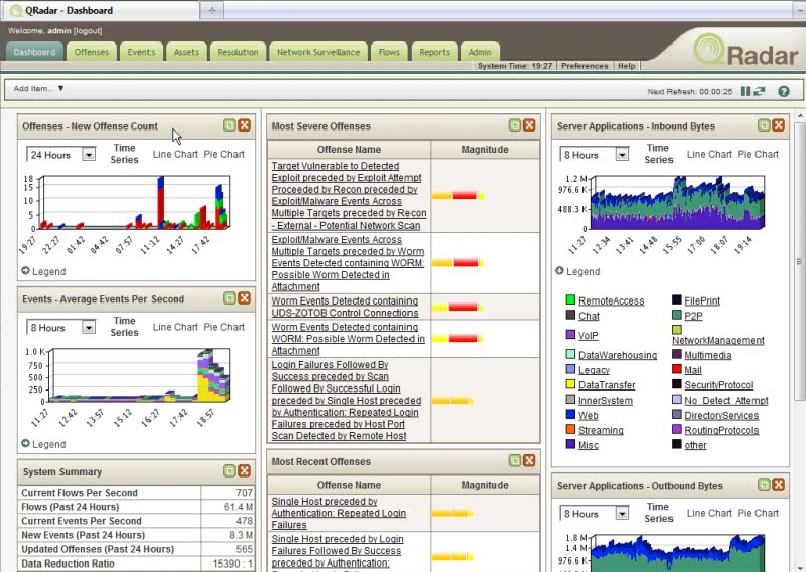
 In their business unit
In their business unit